5 min read
Undoubtedly if you're in tech you've heard about VPNs. What happens when you decide to host your own VPN at home and combine it with the Pi-Hole? Way more site-blocking power than you had before!
So I heard a lot about Wireguard recently and how combined with the Pi-Hole (which I love and already have), you can take your network-wide ad- and telemetry-blocking on the go! My friend had already written up a blog post about it for his setup so this post will cover mine specifically as I did run into some gotchas.
The Setup
The Host
I have my pi-hole running on a Raspberry Pi 3B. You can read more about how awesome the Pi-Hole is here (TODO: insert link later), but as a quick TL;DR: you give it a file of IPs associated with unwanted sites ad like www.googleadservices.com or telemetry websites and when a device asks the Pi-Hole for the IP associated with the site, it will "blackhole" it, making the content for that site not get sent, resulting in no ads!

I recently got another Raspberry Pi for Christmas and was thinking of using that but the RasPi 3B has enough compute to run both the Pi-Hole and a VPN server so I decided to use the Pi-Hole RasPi as the host.
The Router
For my router, I use the Google OnHub router. You can read more about it here (TODO: insert link later) but it's hands down my favorite router as it makes port forwarding covered later here stupid easy.
Setting up Wireguard
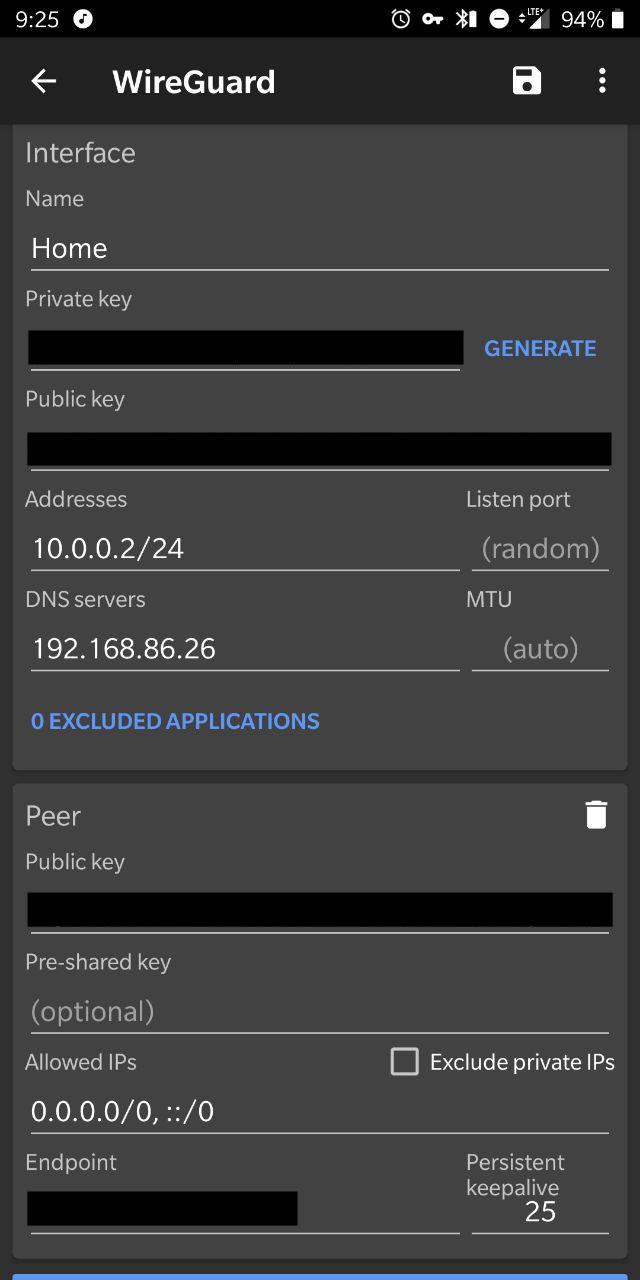
The GitHub README for Wireguard is pretty thorough. I was able to set up the server itself without issue. The interesting part is when the client setup comes in. I'm an Android user so I grabbed the Wireguard app off the Google Play Store. For an unreleased app it's pretty decent -- it's even got a dark mode!
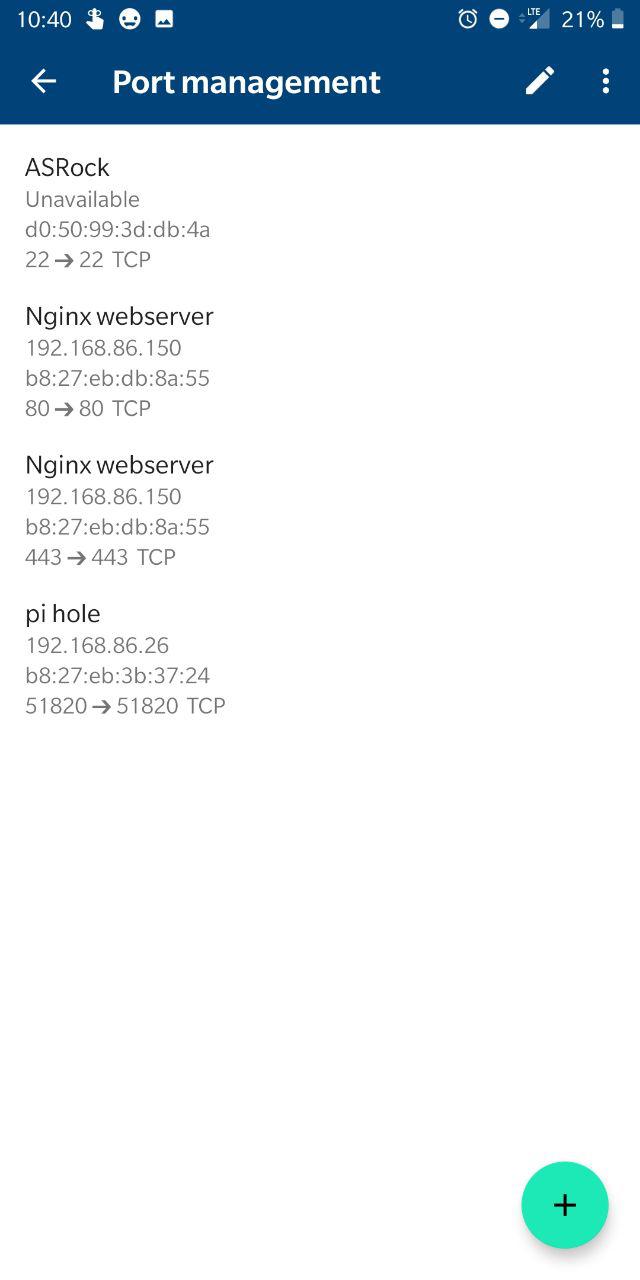
You'll also need to do port forwarding on your router. This is where the greatness of the OnHub router comes in.
From the main page in the app, go to Settings (on the right) > "Networks and General" > "Advanced networking" > "Port management". Then hit the green "+" icon in the bottom left and click the IP of the machine you're running Wireguard on. Hit Next, and then set the internal and external port to be whatever you used for the port on the server's wiregaurd configuration. You'll need to pick UDP only since Wireguard runs on UDP. After setting up the server, client(s), and port forwarding, you should be good to go... unless you of course run into gotchas like I did.
Is This Thing On?
So after following the README in the repo and my friend's guide on setting up Wireguard, everything looked right on the client and server configuration-wise. I also knew Wireguard was running on the server with sudo wg. Excitedly, I hopped off our WiFi, flipped the switch in the Wireguard app, went to visit a site in Chrome aaaand... nothing. So why couldn't I reach any website on the VPN I had just set up? Thus began troubleshooting...
Rootin' Tootin' Troubleshootin'
By the time I had gotten to this phase it was already 11 pm and I was pretty tired. I thought maybe getting some shuteye would be best as I might figure out the answer subconsiously and wake up with the solution. I was half right.
I busted out what Linux-foo I knew to see where it could be breaking after double checking that my keys for the server and client configuration were correct. First up was nmap:
Marshmallow-chan:~ ashleydumaine$ sudo nmap -sU -p 51820 192.168.86.26
# ^ yes that is a Mob Psycho 100 reference
Password:
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-30 01:05 EST
Nmap scan report for 192.168.86.26
Host is up (0.0036s latency).
PORT STATE SERVICE
51820/udp open|filtered unknownOkay so the server should be able to receive packets.
After messing around on Termux on my phone long enough to realize that I can't run nmap with -sU since that requires root on my phone (which I don't actually want) and promptly running the command on my laptop instead as above, I was sufficiently tired to call it a night.
The next morning after leaving for work, I decided to try DNS lookup while on the VPN. I figured something had to be choking there if the client configuration was otherwise good. Interestingly, I was able to hit the Pi-Hole's IP from the browser. Using nslookup/ ping it seemed Google's nameservers were reachable as well and using their nameservers I was able to resolve the IP of websites. So why was it that things wouldn't resolve in Chrome? The answer was seemingly obvious: the nameserver for the client.
dig @192.168.86.26 +short NS google.com
;; connection timed out; no servers could be reachedI couldn't figure out why on my home network I could add 192.168.86.26 in the DNS configuration without issue AND why I could hit 192.168.86.26 from the VPN without issuen but the DNS lookup was failing anyway. Then it dawned on me: most things on my home network use the OnHub router for their main / only DNS nameserver. The OnHub itself acts as a DNS server, but it has its own nameserver list (the Pi-Hole being the primary).
For the sake of hell why not, I swapped the DNS IP in the Wireguard app to the OnHub router's IP and BAM, it magically worked.
Why did it fail? It might have to do with running the nameserver (the Pi-Hole) on the same machine as the VPN server.
TL;DR: you might need to set the DNS in the Wireguard app to be the IP of your router if you're running Wireguard on the same machine as Pi-Hole.
Conclusion
After an hour of setup and a couple hours of head-scratching, I had my own ad-blocking on the go. Even for the minor trouble it was worth, I highly recommend setting up your own Wireguard VPN server, especially if you also have a Pi-Hole so you can browse the net in peace.
