4 min read
(From last time): Undoubtedly if you're in tech you've heard about VPNs. What happens when you decide to host your own VPN at home and combine it with the Pi-Hole? Way more site-blocking power than you had before!
So I wrote up a post a while back about Wiregaurd and how to get it working with the Pi-Hole. At some point later down the line even though nothing changed with the configuration, it stopped working. After much troubleshooting with others it was determined the best path forward would be either to move Wireguard onto an Ubuntu server -- or switch to a different VPN server and client like I did. I ended up going with PiVPN for the server and OpenVPN Connect for the client.
For those curious of my issue with Wireguard, see the below 2 (currently open) issues:
Why PiVPN?
I wanted an easy-to-set up VPN solution specifically for the Raspberry Pi. It's handles the tricky parts of OpenVPN for you including installation, configuration, and management. There are apparently other scripts / projects meant to accomplish the same goal, but this particular one I've seen recommended on several pi-hole discussion threads. So far I have no complaints about it. We'll see in a few months if the sporadic issues pop up again like with Wireguard but fingers crossed this is my new ad-blocking-on-the-go solution.
The Setup
The Host
I have my pi-hole running on a Raspberry Pi 3B. You can read more about how awesome the Pi-Hole is here, but as a quick TL;DR: you give it a file of IPs associated with unwanted sites ad like www.googleadservices.com or telemetry websites and when a device asks the Pi-Hole for the IP associated with the site, it will "blackhole" it, making the content for that site not get sent, resulting in no ads!
The RasPi 3B has enough compute to run both the Pi-Hole and a VPN server so I decided to use the Pi-Hole RasPi as the host.
The Router
For my router, I use the Google OnHub router. You can read more about it here, but it's hands down my favorite router as it makes port forwarding covered later here stupid easy.
Setting up PiVPN + OpenVPN Connect
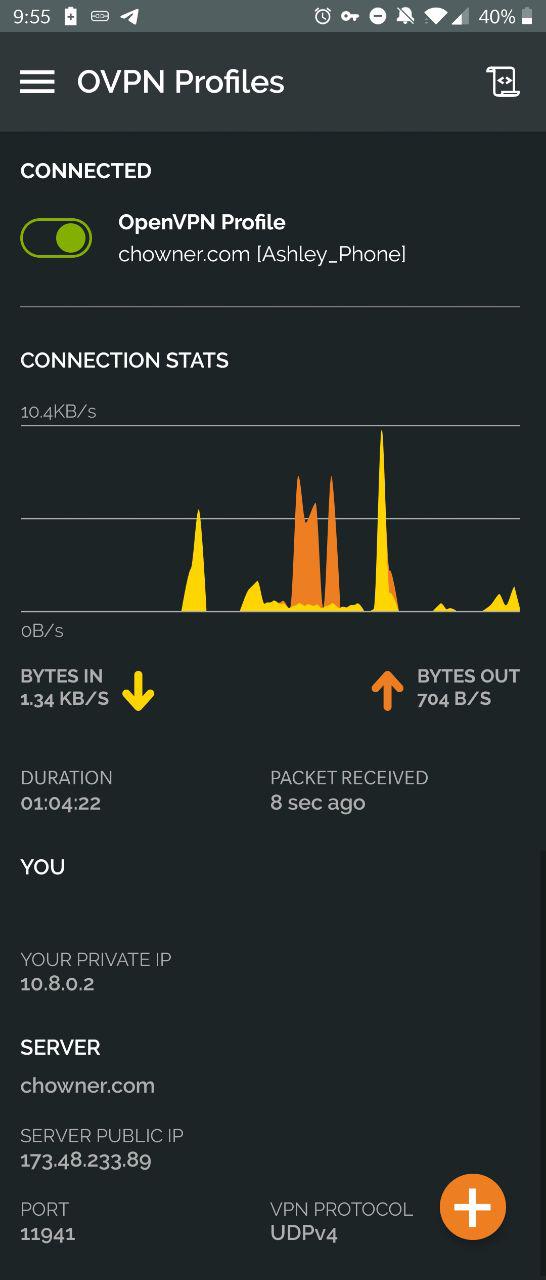
The GitHub README for PiVPN is pretty thorough. I was able to set up the server itself without issue. The interesting part is when the client setup comes in. I'm an Android user so I grabbed the OpenVPN Connect app off the Google Play Store. The app is pretty nifty -- it's even got a dark theme like the Wireguard app (and many more settings too)!
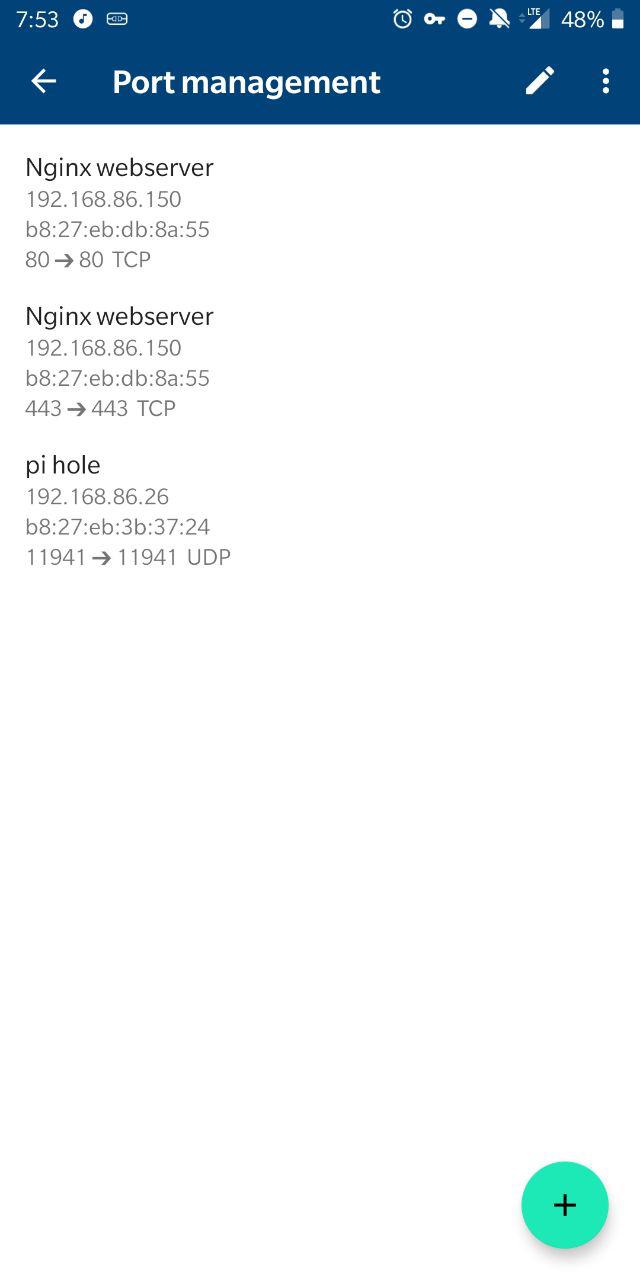
You'll also need to do port forwarding on your router. This is where the greatness of the OnHub router comes in.
From the main page in the app, go to Settings (on the right) > "Networks and General" > "Advanced networking" > "Port management". Then hit the green "+" icon in the bottom left and click the IP of the machine you're running PiVPN on. Hit Next, and then set the internal and external port to be whatever you used for the port on the server's wiregaurd configuration. You'll like want to pick UDP since that is the default for PiVPN (unless for some reason you picked TCP during your server setup). After setting up the server, client(s), and port forwarding, you should be good to go! ... just kidding, there's a couple gotchas you'll need.
Is This Thing On?
So after following the README in the repo, everything looked right on the client and server configuration-wise. I also knew OpenVPN was running on the server with systemctl status openvpn. Excitedly, I hopped off our WiFi, flipped the switch in the OpenVPN app, went to visit a site in Chrome aaaand... nothing. So why couldn't I reach any website on the VPN I had just set up? Thus began troubleshooting...
Yay! No ads again on mobile! \(^_^)/
Rootin' Tootin' Troubleshootin'
This actually wasn't nearly as bad as with Wireguard because the pi-hole docs cover if you want to run OpenVPN on the same Pi! Check out the docs here. In my case though, I set pihole -a -i local instead of pihole -a -i all. Don't forget to install a firewall on your Pi if you haven't already!! (sudo apt-get install ufw) I also didn't need to run a reconfigure since my pi-hole interface was already eth0.
Conclusion
After about a half hour, I had my own ad-blocking on the go that reliably worked. After all the trouble I had with Wireguard sporadically failing, I highly recommend setting up your own PiVPN server, especially if you also have a Pi-Hole so you can browse the net in peace.
